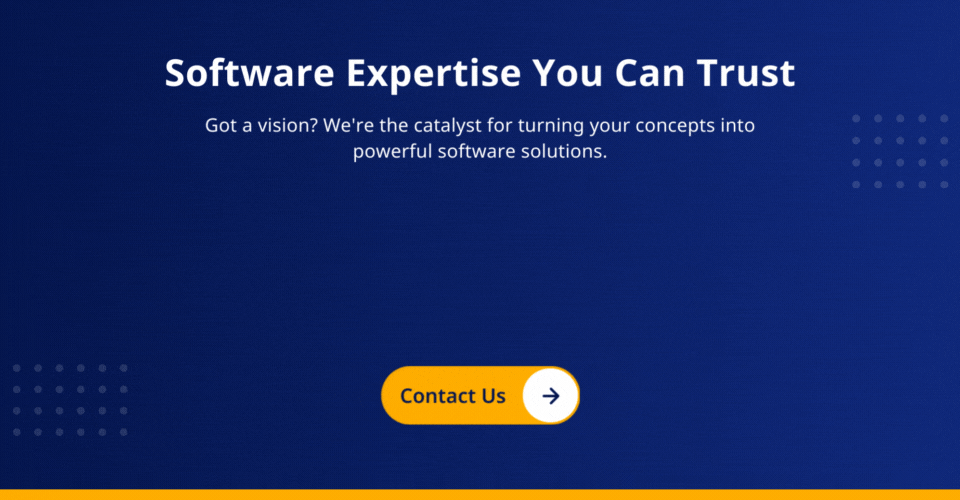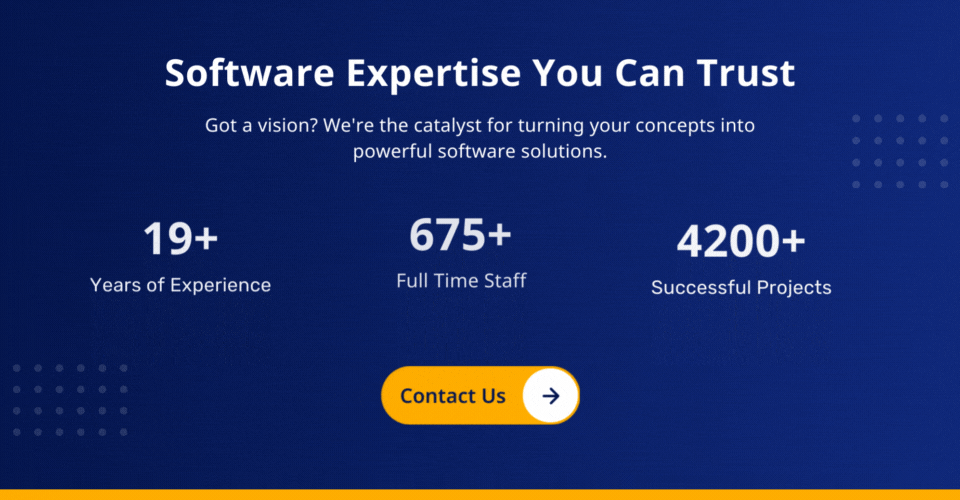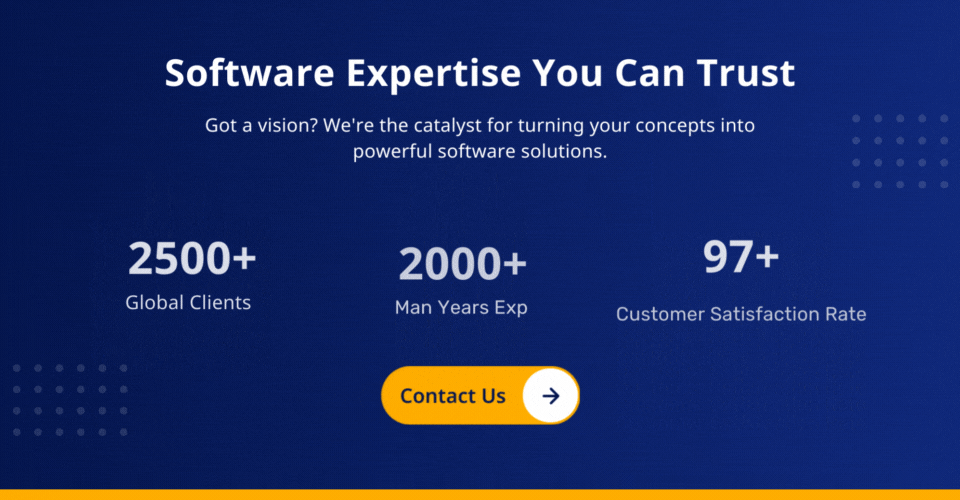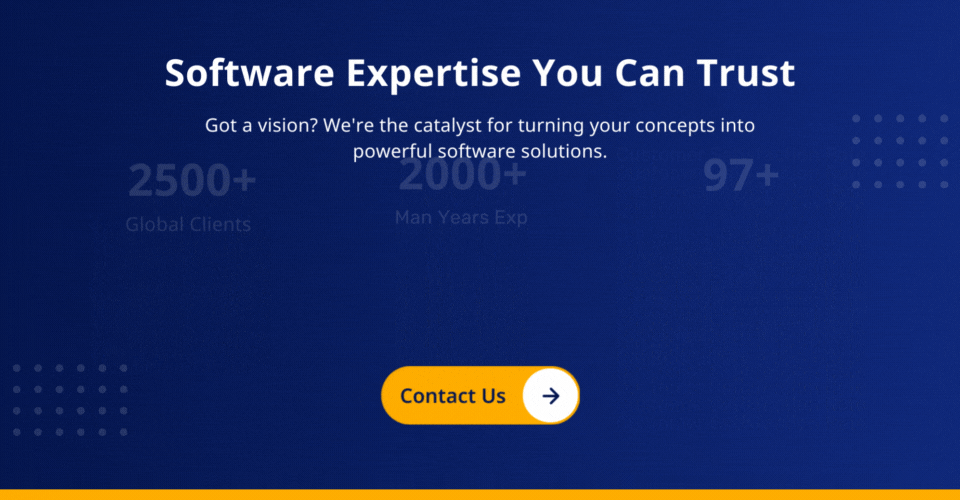
Are you aware?
- The worldwide cybercrime injury goes to attain 10.5$ trillion by 2025.
- The world might want to safe approx. 330 bn new software program code strains within the 12 months 2025.
- The cyber insurance coverage market will hit 14.8$ trillion by 2025, in accordance with the identical supply.
On this digital period of contemporary companies, cyber threats are spreading at an alarming price. It has already risen by over 400% lately. The truth is, international cybersecurity spending goes to exceed $1.75 trillion cumulatively.
Therefore, conventional safety measures are not adequate to guard delicate information & methods.
For this reason superior menace detection has grow to be the necessity of immediately’s hour. It’s an developed strategy that makes use of fashionable instruments/applied sciences to establish & neutralize potential threats earlier than they trigger main damages.
This detailed information discusses how superior menace detection strengthens cybersecurity through 5 highly effective methods of defending & defending precious information in an more and more digital enterprise world.
An Overview of Superior Risk Detection
Superior menace detection helps in figuring out & mitigating extra dangerous cyber threats within the cybersecurity area. This know-how makes use of methods/instruments to guard towards potential breaches.

Right here, we’ve got listed some core parts of superior menace detection and the way they work to extend safety:
Sandboxing is a safety strategy that isolates suspicious recordsdata/packages in a managed surroundings separate from the main digital community. This enables safety groups to securely analyze the habits of probably dangerous code with out affecting system integrity.
By working the code in a digital area, sandboxing can detect and neutralize threats earlier than they penetrate the community, guaranteeing that solely protected, endpoint safety and verified recordsdata are allowed by means of.
UpgradeYour Cyber Defenses!
Expertise the way forward for cybersecurity with superior menace detection.
This strategy includes monitoring & analyzing the habits of customers, community site visitors, and methods to establish anomalies that largely point out a safety menace.
In contrast to conventional signature-based menace detection strategies, which depend on varied identified menace patterns, behavioral evaluation detects new/unknown threats by recognizing uncommon patterns/actions.
This proactive strategy allows the identification of refined assaults like zero-day exploits which may evade typical detection strategies.
This strategy constantly scans the community to establish any signal of malicious exercise. These methods use AI/ML algorithms to investigate information in actual time, establish developments, and establish patterns that point out a menace.
Organizations reply to potential safety incidents extra rapidly & effectively by automating the detection course of. They really decrease the impression of any breach. Automated monitoring additionally helps in lowering the workload on devoted software program groups. Therefore, it permits them to deal with extra strategic duties.
Embedding the above-discussed superior menace detection methods into cybersecurity options can considerably increase an organization’s defenses. Therefore, companies can keep away from evolving threats and defend their crucial property from any kind of cyber assault.
Sorts of Superior Risk Detection Options
The next instruments/applied sciences are important for figuring out & mitigating potential threats earlier than they trigger any important injury. Take a look at a few of the most influential open-source menace detection options out there available in the market:

1. Open Supply Safety: OSSEC is a scalable, complete, and versatile open-source host-based intrusion detection system. It screens & analyzes actions on varied methods viz. log evaluation, Home windows registry monitoring, integrity checking, and so forth.
2. TheHive Challenge: It’s an open-source incident response platform designed to assist cybersecurity professionals collaborate & handle safety incidents effectively. It integrates seamlessly with totally different menace detection instruments and gives a strong interface.
3. osQuery: It’s an working system instrumentation framework that enables customers to question all forms of features of their working methods utilizing SQL-based queries. Developed by Fb, it gives detailed insights into system configuration and standing.
4. OSSECSnort: It’s a broadly used open-source community intrusion detection and prevention system. It analyzes community site visitors in real-time to seek out potential safety threats based mostly on a complete algorithm.
5. Nessus: Though not fully open-source, it presents a free model with in depth vulnerability evaluation options. It scans methods for vulnerabilities that attackers may exploit & gives detailed stories.
High 5 Methods Superior Risk Detection Strengthening Cybersecurity
Take a look on the prime methods or web site safety checklists that superior menace detection use for dependable cybersecurity and constructing safe functions:
1) Proactive Risk Identification
Proactive menace identification includes detecting potential safety threats earlier than they will exploit vulnerabilities or trigger hurt. It permits organizations to handle threats early & forestall important injury, thus providing excellent threat administration in software program growth.
Methods Used
There are numerous superior menace detection leverages a number of refined methods:

- Machine Studying: ML algorithms analyze massive information to establish patterns & predict potential threats.
- Behavioral Evaluation: Monitoring consumer & system habits to detect any kind of anomaly that signifies malicious exercise.
- Anomaly Detection: Figuring out deviations from commonplace patterns that would signify a safety menace.
Advantages
These methods collectively improve cybersecurity in software program growth by:
- Figuring out threats of their early phases. It additional permits for swift motion.
- Decreasing the window of alternative for cyber attackers to use vulnerabilities.
- Minimizing potential injury & disruption to enterprise operations.
Therefore, organizations keep forward of cyber threats & keep a strong safety posture by incorporating these superior strategies.
Additionally learn: Integrating AI And Machine Studying Into Enterprise Operations
2) Actual-Time Monitoring & Response
Actual-time monitoring and response have grow to be important parts of a strong cybersecurity technique. This strategy permits organizations to detect & tackle potential threats as they come up, thus, minimizing injury & sustaining the integrity of their methods.
Steady Surveillance
Steady surveillance allows corporations to watch their methods, networks, and information continually. This proactive strategy ensures that any uncommon/suspicious exercise is recognized instantly.
In contrast to conventional safety data and occasion administration (siem), real-time monitoring gives a dynamic & up-to-the-minute view of the menace panorama. This enables safety groups to identify anomalies and potential breaches as quickly as they happen.
Quick Response
Actual-time response capabilities are very important for compabies to behave swiftly in mitigating threats. When a possible menace is detected, an instantaneous motion is taken to comprise & neutralize it earlier than it turns into a full-blown safety incident. This might contain blocking malicious site visitors, isolating affected methods, or deploying patches & updates to susceptible areas.
Swift response occasions are a key differentiator in sustaining a resilient cybersecurity posture.The flexibility to reply rapidly not solely reduces the menace’s impression but additionally helps protect the group’s popularity & buyer belief.
Case Research
Organizations can successfully counteract threats and safeguard their digital property by sustaining steady surveillance & having the potential to behave instantly. A number of incidents spotlight the effectiveness of real-time monitoring & response in stopping breaches:
1. Goal Information Breach Prevention
A significant retail chain detected uncommon community exercise by means of its real-time monitoring methods. The safety staff acted swiftly to isolate the affected methods & hint the supply of the anomaly. This turned out to be an tried information breach.
By responding instantly, the corporate was in a position to forestall the attackers from misusing delicate buyer information. This will save tens of millions in potential losses & reputational injury.
2. Monetary Establishment Cyber Protection
A number one monetary establishment safeguards its operations with steady surveillance and real-time response methods. When its monitoring methods flagged suspicious login makes an attempt from abroad, the safety staff rapidly intervened.
They carried out extra authentication measures & blocked the suspicious IP addresses. This might have been a major breach. This immediate motion not solely protected the establishment’s property but additionally maintained the boldness of its shoppers.
3. Healthcare Supplier Ransomware Mitigation
A healthcare supplier’s real-time monitoring system detected uncommon file encryption exercise indicative of a ransomware assault. Quick response protocols have been triggered, isolating affected methods and restoring information from backups.
This speedy intervention minimized downtime & ensured that affected person care was not disrupted, demonstrating the crucial position of real-time response in sustaining operational continuity.
Safe Your Enterprise Right now!
Improve your safety with cutting-edge menace detection options.
3) Enhanced Accuracy with Machine Studying and AI
Organizations can obtain increased accuracy in menace detection, cut back the burden of false positives, and proactively defend towards future cyber threats by using the energy of AI and machine studying.

- AI and Machine Studying: AI/ML have revolutionized menace detection by enabling methods to study from information and enhance over time. These applied sciences analyze huge quantity of data to establish patterns & anomalies which may point out a safety menace.
- Decreasing False Positives: Conventional safety testing companies typically generate quite a few alerts, a lot of which aren’t precise threats. AI/ML algorithms refine the detection course of. This ensures that alerts are extra correct, thus saving safety groups time & sources.
- Predictive Capabilities: By analyzing developments & historic information, these methods predict future assaults and assist organizations put together defenses upfront. This enhances their total safety posture.
Instance:
A number one monetary establishment carried out an AI-driven menace detection system, considerably enhancing its skill to detect and reply to threats. Inside months, the establishment reported a 40% discount in false positives & a 30% enchancment in menace detection accuracy.
4) Complete Risk Intelligence
Superior menace detection methods use varied intelligence sources and malware evaluation methods to know the menace panorama completely. Let’s find out about this beneath:

Risk intelligence is gathered from varied sources, every contributing precious insights:
- Open-Supply Intelligence: OSINT present data from publicly out there sources viz. web sites, social media, and information shops. It gives precious context about rising threats and cybercriminals’ ways, methods, and procedures.
- Darkish Net Monitoring: The darkish net is a hub for illicit actions and a market for stolen information and malware. Monitoring darkish net boards and marketplaces can reveal early warning indicators of deliberate assaults or information breaches. This enables organizations to take proactive measures.
- Shared Databases: Platforms just like the Cyber Risk Alliance and Data Sharing and Evaluation Facilities facilitate the alternate of menace data. This helps organizations keep up to date on the most recent threats and vulnerabilities.
Superior menace detection methods excel in integrating & analyzing information from many alternative sources to create complete menace intelligence.
By combining data from OSINT, darkish net monitoring, and shared databases, these methods can:
- Detect Rising Threats: By analyzing information developments and anomalies, superior methods can establish new threats as they emerge, offering early warnings and enabling proactive protection measures.
- Improve Risk Context: Integrating numerous information sources gives a richer context for every menace, together with the menace actors concerned, their motivations, and their strategies. This context is essential for creating efficient countermeasures.
- Automate Risk Response: With real-time evaluation and integration, superior methods can automate responses to detected threats, comparable to blocking malicious IP addresses or isolating compromised methods, thus minimizing the impression of assaults.
5) Automated Risk Mitigation
By integrating automated menace mitigation into their cybersecurity framework, companies can improve their skill to swiftly and successfully deal with cyber threats. This additionally ensures a strong protection towards evolving cyber challenges.

- Automation in Cybersecurity: It makes use of superior algorithms and machine studying to detect & reply to threats in real-time, considerably lowering the time between detection and motion.
- Automated Incident Response: Automated methods can take predefined actions to mitigate threats with out requiring human intervention.
- Effectivity and Velocity: The first benefits of automation in cybersecurity are effectivity and pace. Automated menace mitigation methods function 24/7, guaranteeing fixed vigilance and speedy response to incidents.
Adaptability to Rising Threats
The world of cyber threats is regularly altering, with new vulnerabilities and assault vectors.This dynamic surroundings requires the prime software program safety suggestions that may adapt rapidly to remain forward of potential assaults.
Nonetheless, there are some static safety options out there within the marklet, however they will rapidly grow to be out of date with time and go away organizations susceptible to new forms of assaults.
That’s why superior menace detection methods make the most of adaptive studying applied sciences viz. machine studying and AI options for IT, to constantly study & adapt to new threats.
- These methods analyze massive quantities of knowledge, establish patterns, and replace their detection algorithms in real-time.
- They acknowledge and reply to novel threats that conventional safety measures may miss.
- They supply strong safety towards the most recent threats in fashionable companies.
Furthermore, Adaptive studying ensures that the safety infrastructure stays efficient towards each identified and unknown threats, thus, offering a proactive protection mechanism that evolves alongside the menace panorama.
Keep Forward of Cyber Threats!
Use superior know-how to safeguard your information.
Case Research of Profitable Implementations
By adopting cutting-edge applied sciences and proactive safety measures, organizations can successfully defend their digital property, guarantee enterprise continuity, and construct belief with their stakeholders.

Listed here are a couple of examples displaying the effectiveness of superior menace detection in strengthening cybersecurity:
1. Monetary Establishment for Proactive Fraud Prevention
A number one monetary establishment confronted steady threats from cybercriminals trying to breach its methods & defraud clients.
By implementing a sophisticated menace detection system that utilized machine studying & behavioral evaluation, the establishment was in a position to monitor transactions in real-time & establish suspicious actions.
Additionally learn: Why Is Machine Studying The Greatest For Fraud Prevention
2. Healthcare Supplier for Ransomware Protection
A big healthcare supplier was focused by a classy ransomware assault that threatened to encrypt affected person information and disrupt operations.
The group had not too long ago deployed a sophisticated menace detection answer with real-time monitoring and automatic response capabilities. The system detected uncommon file encryption actions and instantly remoted the affected methods.
3. E-Commerce Platform for Enhanced Buyer Safety
An e-commerce platform dealing with huge quantities of buyer information wanted a strong answer to defend towards evolving cyber threats.
By integrating darkish net monitoring and OSINT into their superior menace detection framework, the platform may establish and tackle threats earlier than they materialized into full-blown assaults.
4. Authorities Company for Complete Community Safety
A authorities company tasked with defending delicate nationwide information confronted the problem of safeguarding towards a big selection of cyber threats.
Implementing a sophisticated menace detection system with complete menace intelligence capabilities allowed the company to watch its community constantly and reply to threats in real-time.
5. Retail Chain for Securing Level-of-Sale Techniques
A big retail chain skilled repeated makes an attempt to compromise its point-of-sale (POS) methods, placing buyer cost data in danger.
The retailer deployed a sophisticated menace detection answer that utilized sandboxing and behavioral evaluation to watch POS actions. The system rapidly recognized and remoted malware attempting to infiltrate the community.
Optimize Your Cybersecurity Technique!
Implement superior menace detection for complete safety.
Remaining Phrases
As cyber threats develop in complexity & frequency, the necessity for superior menace detection has by no means been extra crucial. By integrating progressive applied sciences & proactive methods, organizations can safeguard their digital property & keep buyer belief.
From real-time monitoring to predictive analytics, the developments in menace detection are reshaping the cybersecurity panorama, making it attainable to detect & neutralize threats earlier than they trigger hurt.
Let’s join with our specialists at ValueCoders (a number one utility testing companies firm in India) as they use these cutting-edge options to fortify defenses and guarantee a resilient and safe future in an more and more digital world.