
Microsoft Defender for Endpoint now makes use of computerized assault disruption to isolate compromised person accounts and block lateral motion in hands-on-keyboard assaults with the assistance of a brand new ‘comprise person’ functionality in public preview.
In such incidents, like these involving human-operated ransomware, risk actors infiltrate networks, transfer laterally after escalating privileges through stolen accounts, and deploy malicious payloads.
In keeping with Microsoft, Defender for Endpoint now prevents attackers’ lateral motion makes an attempt inside victims’ on-premises or cloud IT infrastructure by quickly isolating the compromised person accounts (aka suspicious identities) they could exploit to realize their goals.
“Assault disruption achieves this consequence by containing compromised customers throughout all units to outmaneuver attackers earlier than they’ve the prospect to behave maliciously, akin to utilizing accounts to maneuver laterally, performing credential theft, knowledge exfiltration, and encrypting remotely,” mentioned Rob Lefferts, Company Vice President for Microsoft 365 Safety.
“This on-by-default functionality will establish if the compromised person has any related exercise with every other endpoint and instantly minimize off all inbound and outbound communication, primarily containing them.”
In keeping with Microsoft, when the preliminary levels of a human-operated assault are detected on an endpoint utilizing alerts from numerous Microsoft 365 Defender workloads (together with identities, endpoints, e-mail, and SaaS apps), the automated assault disruption future will block the assault on that gadget.
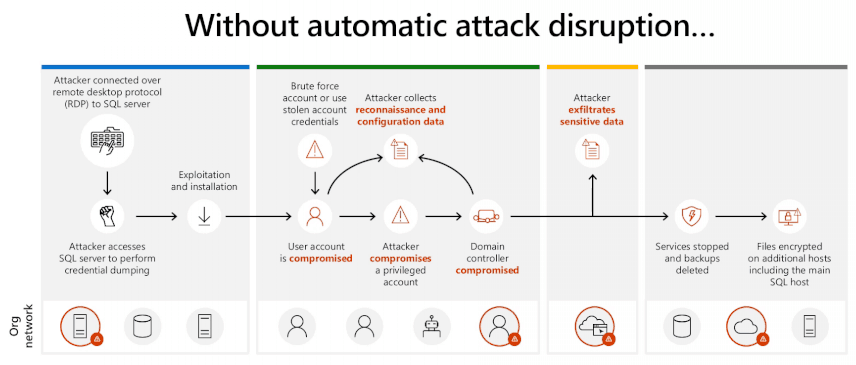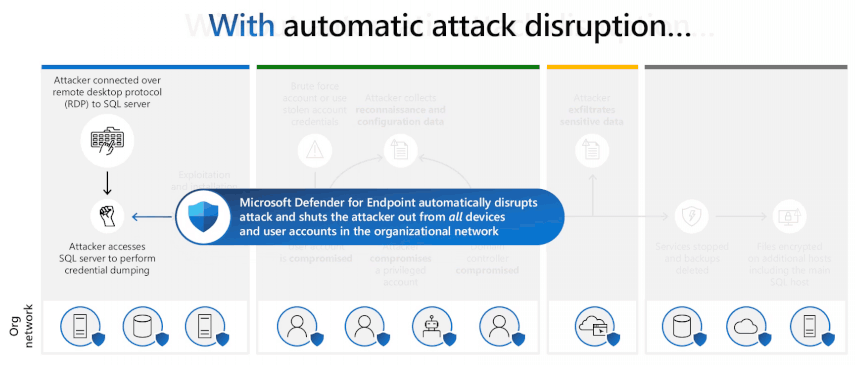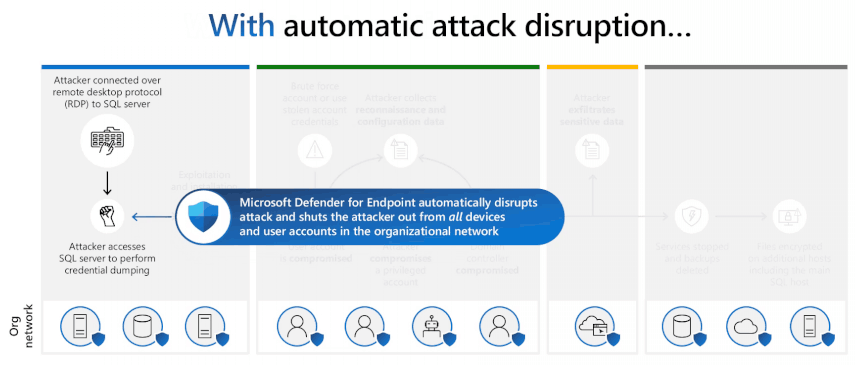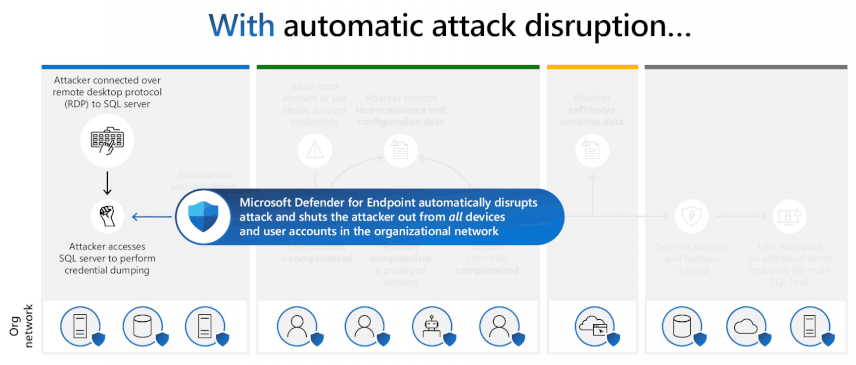
Concurrently, Defender for Endpoint may also “innoculate” all different units throughout the group by blocking incoming malicious visitors, leaving the attackers with no additional targets.
“When an identification is contained, any supported Microsoft Defender for Endpoint onboarded gadget will block incoming visitors in particular protocols associated to assaults (community logons, RPC, SMB, RDP) whereas enabling professional visitors,” Redmond explains in a help doc.
“This motion can considerably assist to scale back the influence of an assault. When an identification is contained, safety operations analysts have additional time to find, establish and remediate the risk to the compromised identification.”
Microsoft added computerized assault disruption to its Microsoft 365 Defender XDR (Prolonged Detection and Response) answer in November 2022 throughout its annual Microsoft Ignite convention for builders and IT professionals.
The potential helps comprise in-progress assaults and isolate affected belongings routinely by limiting lateral motion throughout compromised networks.
“Since August 2023, greater than 6,500 units have been spared encryption from ransomware campaigns executed by hacker teams together with BlackByte and Akira, and even pink groups for rent,” in keeping with Microsoft’s inner knowledge.
Defender for Endpoint can be able to isolating hacked and unmanaged Home windows units since June 2022, stopping malicious actors from transferring laterally by means of victims’ networks by blocking all communication to and from the compromised units.
